Modern systems are no longer isolated applications. They are networks of services, partners, and platforms exchanging data and triggering actions across organizational boundaries. Application-to-Application (A2A) communication has become the backbone of SaaS ecosystems, internal microservices, and B2B integrations.
Despite its importance, A2A security is often underestimated.
Many teams assume that once authentication is in place, an API key, a bearer token, or OAuth, the problem is solved. In reality, authentication is only the starting point. Most real-world A2A incidents are not caused by missing authentication, but by misplaced trust, over-privileged identities, and uncontrolled replay and delegation.
This article examines the most common A2A risks and vulnerabilities, why they occur, and how to reason about them systematically.
What Is A2A, Really?
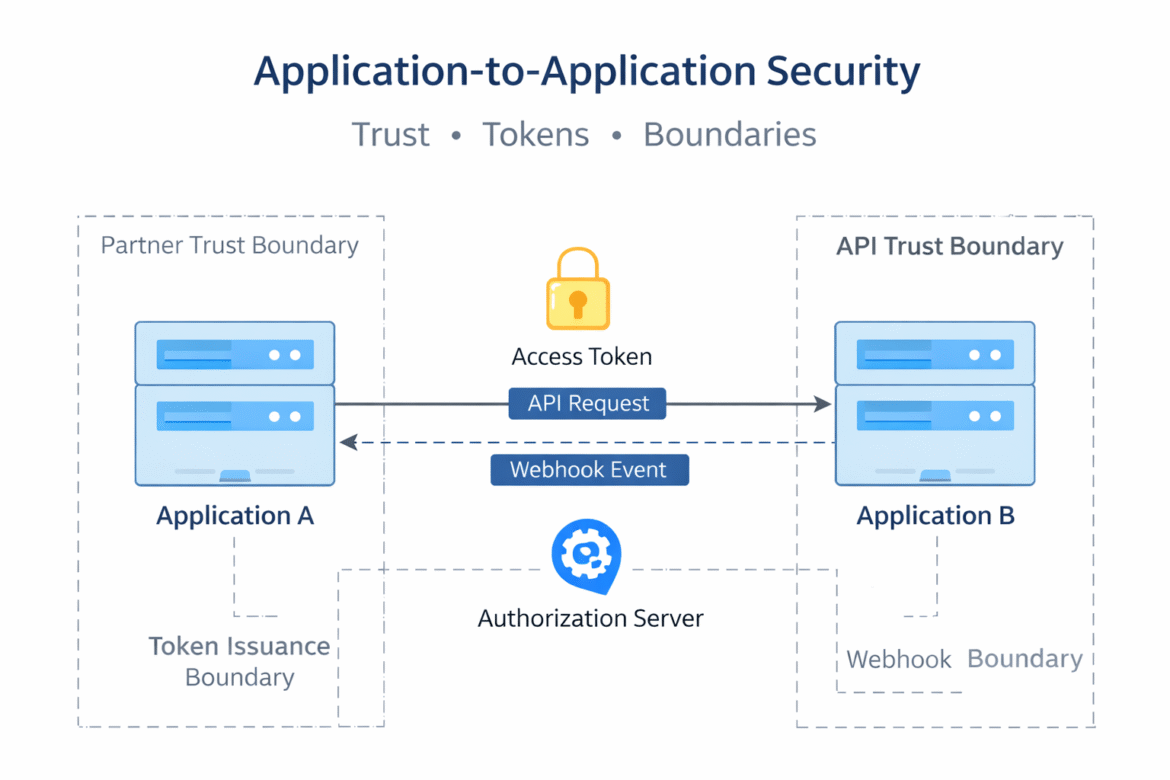
At a high level, A2A refers to one application calling another without a human user directly involved in the interaction.
Typical examples include:
- A backend service calling another internal API
- A SaaS platform integrating with a partner’s API
- An event-driven system delivering callbacks or webhooks
- A batch job pulling data from an external service
Most A2A integrations use:
- OAuth 2.0 client credentials
- API gateways
- Webhooks or message queues
- Service identities instead of user identities
The absence of a human user changes the threat model fundamentally.
The Core A2A Security Problem: Trust Without Context
In user-centric systems, intent is explicit. A user clicks a button, submits a form, or performs an action that can be audited and reasoned about.
In A2A systems:
- Intent is inferred
- Identity is abstracted
- Actions are automated
- Failures propagate quickly
This leads to a recurring anti-pattern:
A trusted service becomes a confused deputy acting on behalf of untrusted or ambiguous input.
Tokens, headers, and service identities carry authority, but they do not inherently carry context, intent, or risk awareness.
Common A2A Risks and Vulnerabilities
1. Token Theft and Replay
Access tokens are often treated as “safe” because they are short-lived. In practice:
- Tokens are logged
- Tokens are cached
- Tokens are copied into debug tools
- Tokens are replayed across environments
Without binding tokens to:
- audience
- scope
- time
- caller identity
a stolen token is often indistinguishable from a legitimate request.
Impact: Unauthorized API access, data exfiltration, and lateral movement across services.
2. Over-Privileged Service Identities
Service accounts frequently have broader permissions than necessary because:
- Fine-grained scoping is hard
- Teams optimize for “it works”
- Permissions grow over time but are rarely reduced
Unlike user accounts, service identities:
- do not notice anomalies
- do not question unusual behavior
- operate continuously
Impact: Small misconfigurations lead to large blast radii.
3. Confused Deputy Attacks
The confused deputy problem is especially common in A2A systems.
A trusted service:
- receives a request
- validates authentication
- performs an action using its own privileges
The service does not verify whether:
- the caller was authorized to request that action
- the action aligns with the original intent
- the downstream effect is safe
Impact: Privilege escalation across services and tenants.
4. Partner Trust Assumptions
In B2B integrations, each side assumes the other enforces security correctly.
Common failures include:
- trusting partner-generated identifiers
- assuming partner token hygiene
- accepting callbacks without verification
- failing to constrain partner scopes
Once trust is implicit rather than enforced, security boundaries blur.
Impact: Cross-tenant data exposure, abuse of shared infrastructure, and contractual risk.
5. Webhook Spoofing and Replay
Webhooks are a special case of A2A communication that often bypass normal security rigor.
Typical issues:
- missing signature validation
- no timestamp or nonce checks
- no replay protection
- public endpoints with weak verification
Because webhooks are inbound, they are frequently exposed to the internet.
Impact: Event forgery, repeated execution, and unauthorized state changes.
6. Lack of Action-Level Authorization
Many APIs validate tokens but do not validate actions.
A token may be valid, but:
- the requested operation may be inappropriate
- the frequency may be abusive
- the timing may be suspicious
Without action-level checks, APIs become brittle under automation.
Impact: Abuse that looks legitimate at the protocol level.
7. Insufficient Auditability
When incidents occur, teams often cannot answer:
- Who called this API?
- On behalf of whom?
- Why was this action allowed?
- What token or scope was used?
A2A systems often lack:
- immutable audit logs
- request-to-action traceability
- partner attribution
Impact: Delayed response, weak forensics, and regulatory exposure.
Why A2A Security Is Harder Than It Looks
A2A vulnerabilities persist not because teams are careless, but because:
- Automation amplifies small mistakes
- Tokens collapse identity and permission into opaque strings
- Ownership is split across teams or organizations
- Failures propagate faster than humans can intervene
Most importantly, A2A systems are architectural, not just technical. Security cannot be bolted on after integration contracts are defined.
Rethinking A2A Security as an Architectural Problem
Effective A2A security starts by answering architectural questions, not tool questions:
- Where does trust change?
- Which service is acting on whose behalf?
- What authority is being delegated?
- What happens if this request is replayed?
- What is the maximum blast radius of failure?
Only after these questions are answered do mechanisms like OAuth, mTLS, or signatures become meaningful.
Closing Thoughts
A2A integrations are no longer edge cases; they are the system.
As systems become more interconnected, the security posture of an application is increasingly defined by how it communicates with others, not by its internal logic.
Understanding A2A risks is less about memorizing vulnerabilities and more about recognizing where trust is assumed rather than enforced.
Threat modeling A2A systems forces that trust into the open and that is where meaningful security begins.

Leave a Reply